In this article you’ll learn about Network security model and its components.
A Network Security Model exhibits how the security service has been designed over the network to prevent the opponent from causing a threat to the confidentiality or authenticity of the information that is being transmitted through the network.
When we send our data from source side to destination side we have to use some transfer method like the internet or any other communication channel by which we are able to send our message. The two parties, who are the principals in this transaction, must cooperate for the exchange to take place. When the transfer of data happened from one source to another source some logical information channel is established between them by defining a route through the internet from source to destination and by the cooperative use of communication protocols (e.g., TCP/IP) by the two principals.
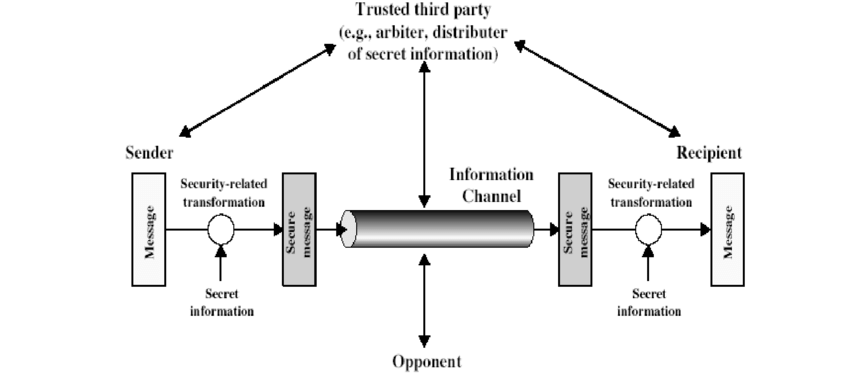
Well, we are concerned about the security of the message over the network when the message has some confidential or authentic information which has a threat from an opponent present at the information channel. Any security service would have the three components discussed below:
- A security-related transformation on the information to be sent.
- Some secret information shared by the two principals and, it is hoped, unknown to the opponent.
- A trusted third party may be needed to achieve secure transmission. For example, a third party may be responsible for distributing the secret information to the two principals while keeping it from any opponent. Or a third party may be needed to arbitrate disputes between the two principals concerning the authenticity of a message transmission.
Model shows that there are four basic tasks in designing a particular security service:
- Design an algorithm for performing the security-related transformation.
- Generate the secret information to be used with the algorithm.
- Develop methods for the distribution and sharing of secret information.
- Specify a protocol to be used by the two principals that make use of the security algorithm and the secret information to achieve a particular security service.
Thank you for reading, If you have reached so far, please like the article, It will encourage me to write more such articles. Do share your valuable suggestions, I appreciate your honest feedback!